Led by Noam Rotem, vpnMentor’s research team discovered a data breach by French consulting firm Bluenove that indirectly exposed thousands of employees and customers from sporting goods giant Decathlon.
By vpnMentor Research Team

The data breach appears to originate from a survey undertaken by Bluenove on Decathlon’s behalf, as part of its “Vision 2030” campaign.
While Decathlon is not responsible for this data breach, it’s the second time in just over a year that we’ve discovered a leak affecting the company. In February 2020, we reported on a breach involving Decathlon Spain.
By not thoroughly vetting Bluenove’s data privacy standards before hiring the firm, Decathlon has inadvertently exposed a big chunk of its workforce to fraud and various forms of online threats.
Data Breach Summary
| Companies Involved | Bluenove & Decathlon (Bucket owned by Bluenove, containing Decathlon’s data) |
| Headquarters | France (both) |
| Industry | Sporting Goods; Corporate affairs |
| Size of data | 61 MB |
| No. of files | 7,883 |
| No. of people exposed | 7,883 |
| Date range/timeline | March – November 2020 |
| Geographical scope | Potentially global (countries with Decathlon branches) |
| Types of data exposed | PII data; employee details |
| Potential impact | Rauf & phishing; legal actions; bad publicity |
| Data storage format | Misconfigured AWS S3 Bucket |
Company Profile
Bluenove is an ‘open innovation’ and ‘collective intelligence’ consulting company based in Paris, France, and Montreal, Canada.
The company works with public and private organizations to help them develop strategic planning based on large-scale collaboration with stakeholders.
Aside from Decathlon, Bluenove clients include the European Commission (part of the EU), Medtronic France, EDF Energy, and Société Générale bank.

Decathlon is a French sporting goods retailer. The company has over 1,600 stores across 56 countries and employs more than 96,000 people.
Its revenue in 2019 was $13.3 billion.
Timeline of Discovery and Owner Reaction
- Date discovered: 9th March 2021
- Date vendors contacted: 16th March 2021
- Date of additional contact attempts: 22nd March and 5th April 2021
- Date AWS Contacted: 22nd March 2021
- Date of Response: 22nd March 2021
- Date Decathlon contacted: 12th April 2021
- Date Decathlon replied: 12th April 2021
- Date of Action: 13th April 2021
Sometimes, the extent of a data breach and the data’s owner are obvious, and the issue is quickly resolved. But rare are these times. Most often, we need days of investigation before we understand what’s at stake or who’s exposing the data.
Understanding a breach and its potential impact takes careful attention and time. We work hard to publish accurate and trustworthy reports, ensuring everybody who reads them understands their seriousness.
Some affected parties deny the facts, disregarding our research or playing down its impact. So, we need to be thorough and make sure everything we find is correct and accurate.
In this case, Bluenove was using a misconfigured Amazon Web Services (AWS) S3 bucket to store its files. S3 buckets are a hugely popular form of cloud storage used by 100,000s of companies across the globe. However, they require users to set up security protocols manually.
Bluenove failed to configure the security settings on its S3 bucket, leaving it open and publicly accessible. Furthermore, the S3 bucket contained the company’s name, exposing it as the owner immediately.
After discovering the S3 bucket, our team undertook a thorough investigation of the data stored within. We quickly identified Decathlon as the true owner of the data, which had been collected and stored for the company by Bluenove.
Once our investigation was over, we contacted Bluenove and AWS to notify each party of the data breach. Despite two follow-up emails to Bluenove and one reply from the company’s chief operations and products officer, the vulnerability still hadn’t been closed a month later.
We decided to contact Decathlon directly and notify it of the breach. They replied quite quickly, asking for information about the nature of the breach, and the next day we saw that the breach was finally secured. Decathlon reached out once more shortly after.
Example of Entries in the S3 Bucket
Bluenove’s S3 bucket contained 7,883 files, totaling 64 megabytes. While this is a relatively small data breach compared to others we discovered and reported on, it still compromised the security and privacy of over 7,000 people.
It appears that Bluenove collected the data from a survey of Decathlon staff and customers as part of its ‘Vision 2030’ campaign.
The data contained answers submitted by 193 people surveyed, including their Personally Identifiable Information (PII) Data. However, most of the data (7,000+ records) were simply records of employee and customer data with no apparent relationship to the surveys.
The employee private personal user data we viewed included:
- Full names
- Usernames
- Phone numbers
- Email addresses
- Countries and cities of residence
- Authentication tokens
- Photos
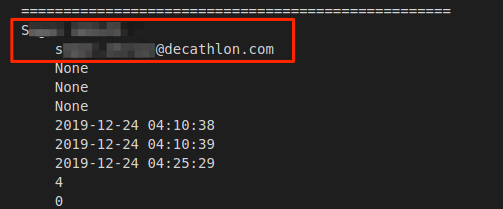
Decathlon employee PII data
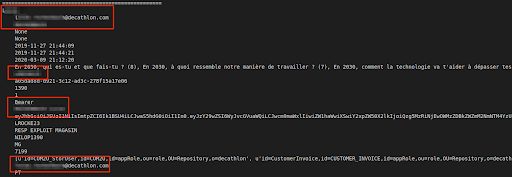
Additional Decathlon employee PII data
The PII data for members of the public also included:
- Full names
- Email addresses
- Country and city of residence
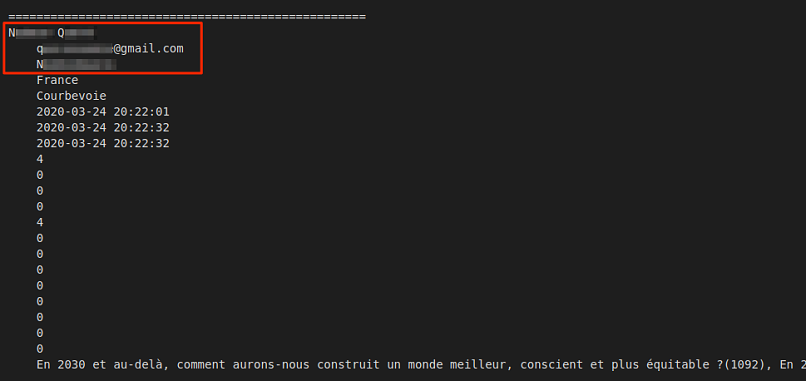
Decathlon customer PII data
In total, 7,883 people were exposed in the data breach. It’s difficult to separate these into customers and employees without viewing every individual entry, which is against our ethics.
However, the data breach may have compromised close to 10% of Decathlon’s workforce.
Furthermore, the S3 bucket also contained security tokens (also known as bearer tokens) that could have allowed additional access to private accounts or other internal areas within Decathlon’s system. However, we didn’t attempt to use these tokens for ethical reasons, but we urge Decathlon to investigate it further to prevent abuse by malicious 3rd parties.
Data Breach Impact
By not securing its client’s data adequately, Bluenove compromised Decathlon, its employees, and the company itself, exposing each party to a wide range of issues.
For Decathlon’s Employees and Customers
Had malicious hackers gained access to this data, they could have targeted 1,000s of Decathlon staff and customers with various forms of online fraud and viral attack.
By combining an individual’s PII data, information about the surveys taken, and other details exposed, hackers could have crafted highly effective phishing campaigns posing as Bluenove or Decathlon via email or phone calls.
In doing so, they could easily convince people to provide even more sensitive data for fraudulent purposes (such as financial information) or clicking links embedded with malware, spyware, or another form of malicious software.
For Decathlon
If hackers successfully used this data breach to defraud Decathlon employees, the company would have faced severe repercussions. Staff at the company could lose trust in the employer and try to take legal action against them, despite Decathlon not being directly responsible. Customers would be reluctant to engage with the company online in the future – a critical issue as so much commerce happens online now.
The bad publicity generated from exposing its employees and customers to hacking and fraud could also create considerable marketing and PR headaches.
For Bluenove
For a company that prides itself on utilizing cutting-edge software, a data breach like this could seriously discredit Bluenove. Clients and partners may be reluctant to engage a consulting firm that fails to secure private data safely and leaks it online and has no protocols in place for addressing data leaks when they’re reported.
The company will need to take steps to ensure this never happens again, and assure potential clients it has learned from its mistakes.
Finally, as Bluenove is based in France and leaked data belonging to Decathlon employees spread across the European Union, it falls within the jurisdiction of GDPR. The company will be expected to take specific steps to mitigate this data breach’s impact or face considerable fines and penalties.
Advice from the Experts
Bluenove could have easily avoided exposing Decathlon’s data if it had taken some basic security measures. These include, but are not limited to:
- Securing its servers.
- Implementing proper access rules.
- Never leaving a system that doesn’t require authentication open to the internet.
Any company can replicate the same steps, no matter its size.
For a more in-depth guide on how to protect your business, check out our guide to securing your website and online data from hackers.
Securing an Open S3 Bucket
It’s important to note that open, publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
In Bluenove’s case, the quickest way to fix this error would be to:
- Make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.
For Decathlon Employees and Customers
If you work or shop at Decathlon and are concerned about how this breach might impact you, contact the company directly to determine what steps it’s taking to protect your data.
To learn about data vulnerabilities in general, read our complete guide to online privacy.
It shows you the many ways cybercriminals target internet users and the steps you can take to stay safe.
How and Why We Discovered the Breach
The vpnMentor research team discovered this breach as part of a huge web mapping project. Our researchers use large-scale web scanners to search for unsecured data stores containing information that shouldn’t be exposed. They then examine each data store for any data being leaked.
Our team was able to access this S3 bucket because it was completely unsecured and unencrypted.
Whenever we find a data breach, we use expert techniques to verify the data’s owner, usually a commercial business.
As ethical hackers, we’re obliged to inform a company when we discover flaws in their online security. We reached out to Bluenove to let them know about the vulnerability and suggest ways to make their system secure.
These ethics also mean we carry a responsibility to the public. Bluenove clients and their employees must be aware of a data breach that exposes so much of their sensitive data.
The purpose of this web mapping project is to help make the internet safer for all users.
We have no evidence – and no way of knowing – whether the data in our reports have been accessed or leaked by anyone else; only the database owner can know that.
We do our best to prevent this from happening by reaching out to the companies and ensuring they secure their leaking database as soon as possible.
We never sell, store, or expose any information we encounter during our security research.
About Us and Previous Reports
vpnMentor is the world’s largest VPN review website. Our research lab is a pro bono service that strives to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
Our ethical security research team has discovered and disclosed some of the most impactful data breaches in recent years.
This has included an enormous data breach exposing the data of 10,000s of online shoppers worldwide. We also uncovered separate scams targeting users on Facebook, Instagram, and Spotify. You may also want to read our VPN Leak Report and Data Privacy Stats Report.