Operational Technology encompasses a wide spectrum of functionalities, and its interpretation varies depending on the organization & its alignment with business objectives.
Operational Technology (OT) encompasses a wide spectrum of functionalities, and its interpretation varies depending on the organization and its alignment with business objectives. It is paramount for each organization to establish a clear definition of ‘OT,’ which involves the meticulous identification and classification of OT assets. A recent survey conducted during an ISAC conference revealed that numerous organizations lack a definitive inventory of device types that fall under their OT umbrella.
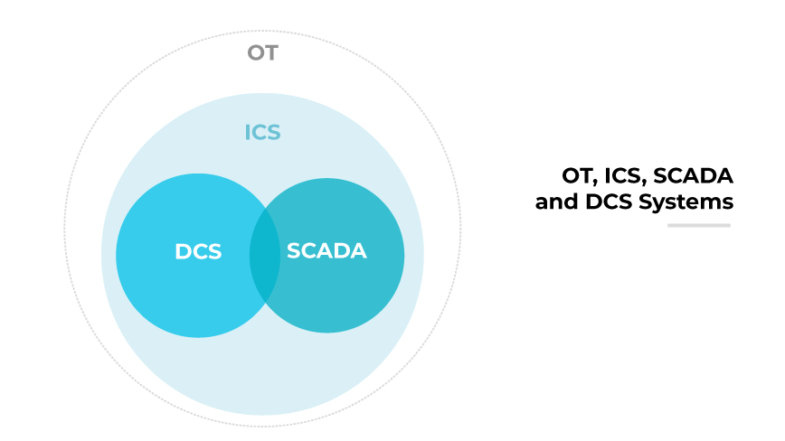
Why it Matters
Recognizing the nature of what we are safeguarding represents the initial stride in mitigating security vulnerabilities within OT systems and environments. Categorizing an asset as OT, IoT, IIoT, IoMT, or conventional IT extends beyond mere terminology; it entails comprehending its purpose, connectivity, performance requisites, support prerequisites, and the potential ramifications in case of malfunction or unavailability.
Questions to answer as an organization would be:
- What function or process does it perform?
- What connectivity does it require?
- What performance needs does the system have?
- Does it make something or just do something?
- Is it an autonomous, manual, or hybrid system?
- What kind of systems and people need to support them?
- What types of data inputs and outputs are required, and what dependencies are required?
- Does it support a critical process or serve a regulatory function?
- What would happen if it wasn’t available or malfunctioned? Can it jeopardize personal safety? Financial or reputational damage?
- Who knows it’s here? Can it be located, seen, touched, communicated with, or maintained?
The Complete Picture
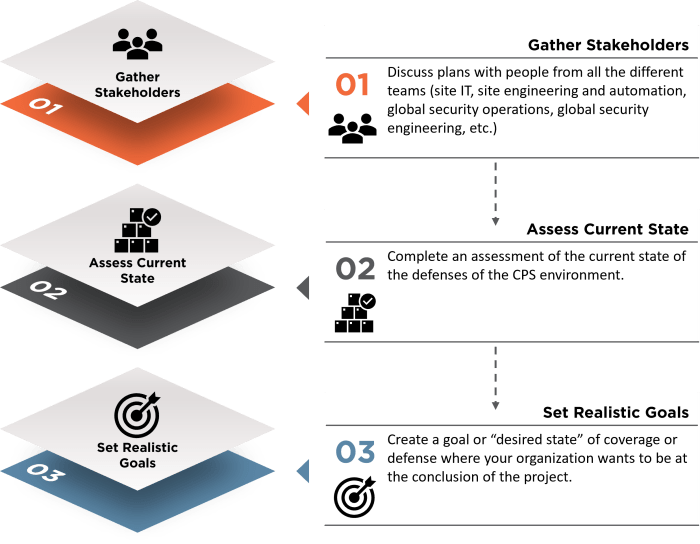
Although OT security monitoring and detection tools offer asset visibility, they constitute just one significant aspect of the broader picture. Once visibility is achieved, organizations must possess the knowledge of how to effectively respond to potential threats without disrupting critical operations. This entails the development and implementation of an OT Incident Response Plan (IRP), comprehension of incident prioritization, and, ultimately, identification of the assets deemed as crown jewels.
How to Start
Answering this question necessitates collaboration among various stakeholders, including security personnel, business representatives, site or plant leads, as well as engineering and automation teams. To delineate the types of assets deemed OT, the initial step involves understanding the systems in place within your organization. This can be achieved through a vendor asset management solution or by maintaining a locally managed Excel file.
Once an inventory of assets is compiled, the next step is to classify these assets as OT based on their respective roles within the organization. This classification process may entail straightforward categorization, such as considering all devices from specific manufacturers as OT.
Alternatively, it could involve a more comprehensive analysis of how these assets are utilized within the business operations.
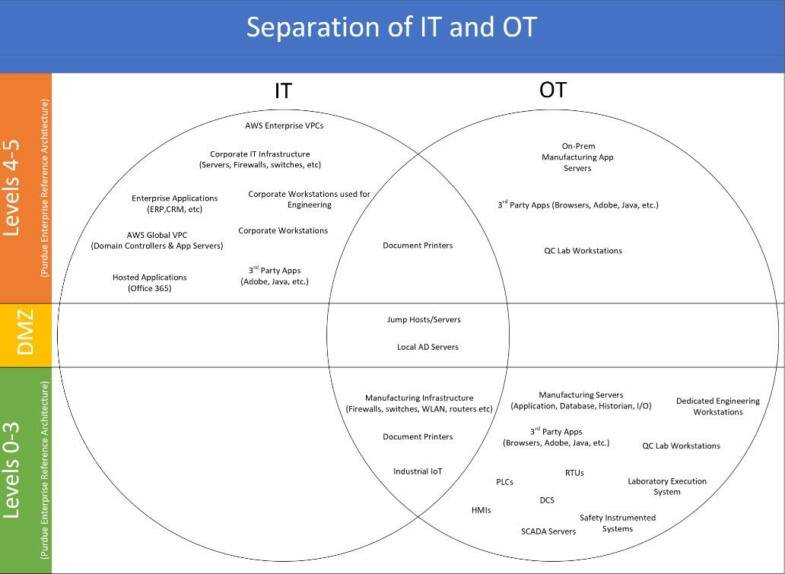
For additional information on the Purdue Enterprise Reference Architecture, visit https://en.wikipedia.org/wiki/Purdue_Enterprise_Reference_Architecture.
When framing OT within your organization, it’s prudent to begin by examining device and system naming conventions, which may include specific syntaxes or nomenclatures like “-mfg” in the hostname. This serves as a foundational step.
A straightforward approach to defining Operational Technology is to consider any device directly involved in the physical production of products as OT. However, it’s crucial to emphasize that this determination is ultimately an organizational decision.
Keeping the classification simple can streamline the process, particularly for IT and Security teams. For instance, considering devices from manufacturing companies such as Rockwell, Siemens, Honeywell, and Advantech as OT provides a clear starting point.
This simplicity allows for easier initial categorization, acknowledging that these devices are directly related to production processes. As maturity in OT management is gained, further refinement can be implemented, including filtering out specific types of systems within these manufacturers instead of treating all OT assets uniformly.
Final Thoughts
The ISA/IEC 62443 standards offer extensive guidance on OT security and are essential resources to acquaint oneself with. However, with the ongoing evolution of “Industry 4.0,” the distinction between OT and IT is becoming progressively less distinct. In light of this, it becomes even more crucial to establish a clear understanding of which assets are considered OT, regardless of whether they reside on the plant floor or in the cloud.
It’s important to emphasize the principle of starting with simplicity and gradually expanding understanding of the OT environment. This approach allows for a more manageable and effective implementation of security measures. As technologies evolve and converge, maintaining a flexible mindset and continually reassessing the classification of assets as Operational Technology will be instrumental in ensuring robust cybersecurity practices.
