The word terrorist network is not new people have been talking about terror networks long before September 11, 2001 despite the discrediting of some of the claims. Despite the new developments in network analysis and network theories.
According to United States Department of State Publication Bureau of Counterterrorism reports that was released in July 2017 Although terrorist attacks and fatalities from terrorism declined globally for the second year in a row in 2016, terrorist groups continued to exploit ungoverned territory and ongoing conflict to expand their reach, and to direct and inspire attacks around the world.
The Islamic State of Iraq and Syria (ISIS) remained the most potent terrorist threat to global security, with eight recognized branches and numerous undeclared networks operating beyond the group’s core concentration in Iraq and Syria. Al-Qaida (AQ) and its regional affiliates remained a threat to the U.S. homeland and our interests abroad despite counterterrorism pressure by U.S. partners and increased international efforts to counter violent Islamist ideology and messaging.
Terrorist groups supported by Iran – most prominently Hizballah – continued to threaten U.S. allies and interests even in the face of U.S.-led intensification of financial sanctions and law enforcement. ISIS attacks outside its territorial strongholds in Iraq, Syria, and Libya were an increasingly important part of its terrorism campaign in 2016. Most of these attacks took place in countries where ISIS has a declared branch, such as Afghanistan, Egypt, Saudi Arabia, and Yemen.
The recruitment of violent extremists through social media remained central to ISIS’s terrorist campaign in 2016. The United States and its partners worked closely with social media and monitoring companies and others to lawfully counter and curtail use of the internet for terrorist purposes.
Due in part to these efforts, ISIS content on the internet declined 75 percent from August 2015 to August 2016, while ISIS-related traffic on Twitter declined 45 percent from mid-2014 to mid-2016. This coincided with a steep reduction in the monthly rate of official visual media releases by ISIS, from 761 in August 2015 to 194 in August 2016, according to a study published by the Combating Terrorism Centre at West Point. Moreover, ISIS had 19 active media outlets at the beginning of 2017, down from at least 40 in 2015, according to another study published by the Council on Foreign Relations.
Identify Terrorist Network.
Due to the new evolving trends of security problems, a new type of intelligence is needed which is called as Social Network Analysis (SNA). To visualize the network, consider the terrorist group composed of thousands of members, hundreds of cells and located in 60 or more countries or is it a much smaller organization which coalesces with other existing organizations when it needs to move people, money or material around the world like the terrorist group.
A terrorist network centrality can be revealed by finding the most tightly connected nodes in a network or finding a person who are likely to hold most information. based on this model we visualise suspicious communication take place in one node and is propagated within groups to other by this node. we identify the flow of communication between different nodes as shown in fig1.
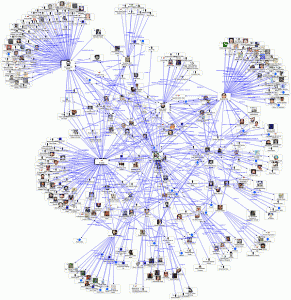
fig1: show the social network regarding social actors (nodes) and their relationships (ties).
To visualise the network more deeply Betweenness Centrality indicate someone holds authority over, or controls collaboration between, disparate clusters in a network like the main group is al-Qaida; or indicate they are on the periphery of both clusters. I also indicate the nodes that lies from the shortest path to other nodes. Closeness Centrality can help you to find out a good broadcaster in a highly connected network. Eigen Vector Centrality score indicates a strong influence over other nodes in the network as shown in fig2.
fig2: shows a main actor that involve to disparate the suspicious information to different node on the basis of centrality measures.
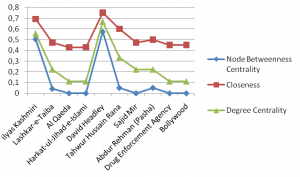
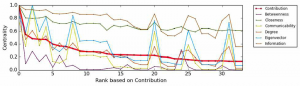
To find out a details information about the main person in a network, we analyse a centrality measurement as shown in fig3.this figure shows a high value of centrality means that high centralization: one node trading with many others means there is a link between different terrorist groups that can be seen in above figure (as Al-Qaida with lashkar-e-taliba and many others).
fig3: Behaviour of the different centrality measures in the network
The need is to visualise and monitoring these types of terrorist groups through social media analysis because,
Social media nowadays about sociology and psychology more than technology.
This article is jointly authored by Sarosh Haider Country Head at Fivecore (Pvt) Ltd and Sehrish Rafiq.
![]()